One Line Generate Ssl Key
How to Generate a Public/Private KeyPair for Use With Solaris Secure Shell
Users must generate a public/private key pair when their site implementshost-based authentication or user public-key authentication. For additionaloptions, see the ssh-keygen(1) manpage.
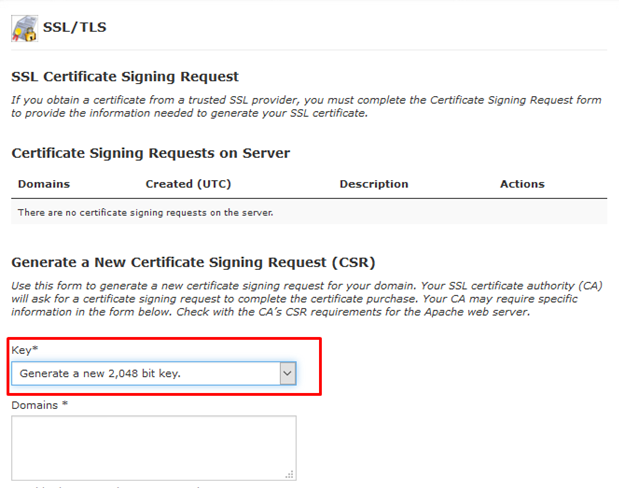
Public key is embedded in the SSL certificate and private key is stored on the server and kept secret. When a site visitor fills out a form with personal information and submits it to the server, the information gets encrypted with the public key to protect if from eavesdropping. Press Enter to create unencrypted key. If you’re the only one that uses the computer, this is safe. Type a password. This will encrypt your key. It’s a good idea to do this if you share your computer with someone else. If you intend to carry the key on a USB stick, definitely use a password here. How to generate private key and CSR from command line This article describes how to generate a private key and CSR (Certificate Signing Request) from the command line. You may need to do this if you want to obtain an SSL certificate for a system that does not include cPanel access, such as a dedicated server or unmanaged VPS. The best way to avoid this is: Create your own authority (i.e., become a CA) Create a certificate signing request (CSR) for the server. Sign the server's CSR with your CA key. Install the server certificate on the server. Install the CA certificate on the client. Jul 09, 2019 Public Key Infrastructure (PKI) security is about using two unique keys: the Public Key is encrypted within your SSL Certificate, while the Private Key is generated on your server and kept secret. All the information sent from a browser to a website server is encrypted with the Public Key, and gets decrypted on the server side with the Private Key. Script for Check SNMP with one-line; create. Script for Creating SSH Keypar with one-line; Script for Creating SSL CSR and Key with one-line; Creating SSL SAN CSR and Key with one-line; fh. Script for fping multiple servers; script for ping multiple servers (fhping.sh) SSH.
Before You Begin
Determine from your system administrator if host-based authenticationis configured.
Start the key generation program.
where -t is the type of algorithm, one of rsa, dsa, or rsa1.
Specify the path to the file that will hold the key.
Bydefault, the file name id_rsa, which represents an RSAv2 key, appears in parentheses. You can select this file by pressing the Return key. Or, you can type an alternative file name.
The file name of the public key is created automatically by appendingthe string .pub to the name of the private key file.
Type a passphrase for using your key.
This passphraseis used for encrypting your private key. A null entry is stronglydiscouraged. Note that the passphrase is not displayed when youtype it in.
Retype the passphrase to confirm it.
Check the results.
Check that the path to the keyfile is correct.
At this point, you have created a public/private key pair.
Choose the appropriate option:
If your administrator has configuredhost-based authentication, you might need to copy the local host's publickey to the remote host.
You can now log in to the remote host.For details, see How to Log In to a Remote Host With Solaris Secure Shell.
Type the command on one line with no backslash.
When you are prompted, supply your login password.
If your site uses user authentication with public keys, populateyour authorized_keys file on the remote host.
Copy your public key to the remote host.
Type thecommand on one line with no backslash.
When you are prompted, supply your login password.
Lotr conquest cd key generator. Whenthe file is copied, the message “Key copied” is displayed.
(Optional) Reduce the prompting for passphrases.
For a procedure, see How to Reduce Password Prompts in Solaris Secure Shell. For more information, see the ssh-agent(1) and ssh-add(1) man pages.
Example 19–2 Establishing a v1 RSA Key for a User
In the following example, the user cancontact hosts that run v1 of the Solaris Secure Shell protocol. To be authenticated by v1hosts, the user creates a v1 key, then copies the public key portion to theremote host.